#
Integrations
The Integrations page allows you to connect BAS with your other products. This empowers BAS to communicate with the third-party provider to determine if it was able to detect the actions taken when a procedure ran. BAS supports integration with the following products.
Carbon Black Cloud CrowdStrike Falcon Microsoft Security SentinelOne Singularity Splunk Cloud (with Splunk Enterprise Security)Splunk Enterprise (with Splunk Enterprise Security)
BAS integrations fall into two categories of capabilities as outlined in the table below.
#
Adding an integration
To add an integration, follow the general steps below. See the sections that follow for your exact integration for any specific details.
Select the Add Integration button at the top right of the page to display the Add Integration right sidebar navigation.
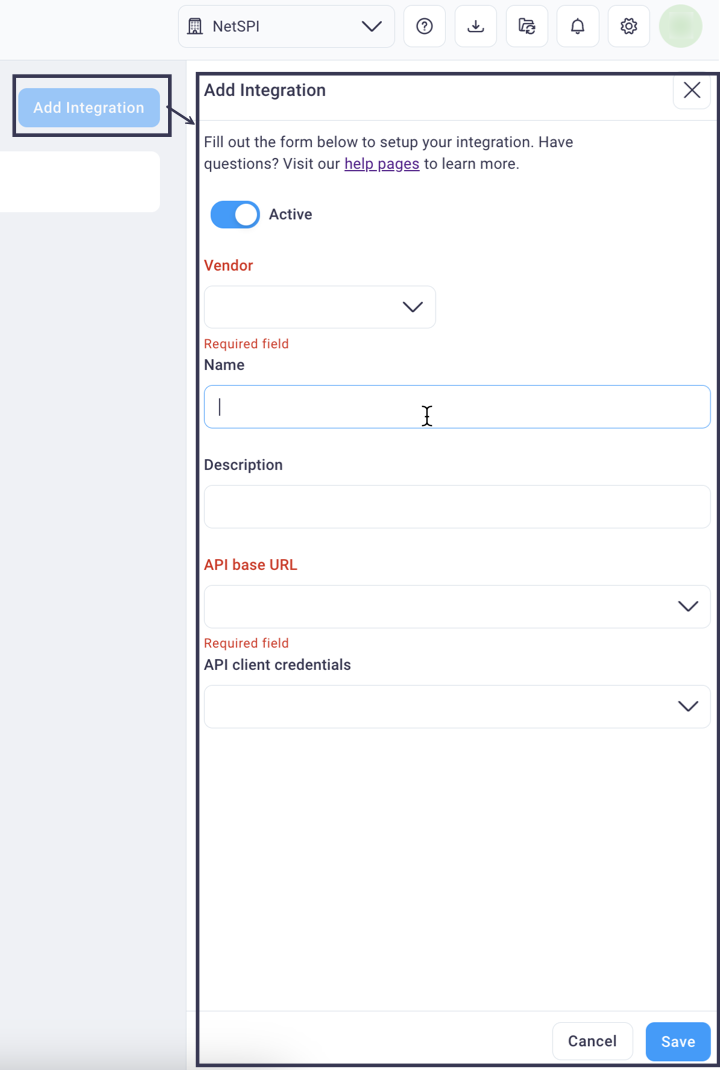
Select the Active slider to set the integration to active (blue) or inactive (gray).
Select the desired integration from the Vendor drop-down list.
Enter a name of your choice in the Name and Description fields.
Enter a value in the Viewing Cutoff Time field. This value, in seconds, represents the look-ahead time since the play was run that events are recorded, capturing or resulting in an event, alert, or detection time.
Each specific integration will also prompt you to select your organization's credentials for the API and its base URL.
See the Credentials page for more information.
#
Carbon Black Cloud integration
Configuring the Carbon Black Cloud integration follows the general instructions above, with the following differences:
- The API base URL field specifies that the Base URL of the Carbon Black API is required
- The Organization Key (located within your Carbon Black Cloud instance)

#
CrowdStrike Falcon integration
Configuring the CrowdStrike integration follows the general instructions above, with the following differences:
- The API base URL field specifies that the Base URL of the CrowdStrike API is required

See the section directly below for a walkthrough of setting up the CrowdStrike Falcon integration.
#
CrowdStrike Falcon integration walkthrough
This integration requires the Oauth Client credential type. Please refer to the CrowdStrike documentation for generating these credentials in Falcon.
Note: When creating an API Client, you will need to enable Read access for the Alerts Scope and Detections Scope.
Select Let's Get Started in the walkthrough below to see how to create a CrowdStrike integration with BAS.
#
SentinelOne Singularity integration
Configuring the SentinelOne Singularity integration follows the general instructions above, with the following differences:
- The API base URL field specifies that the Base URL of the SentinelOne API is required

#
Microsoft Security
Configuring the Microsoft Security integration follows the general instructions above, with the following differences:
- No API base URL field is required, but a Tenant ID value is required

#
Splunk Cloud integration
Configuring the Splunk Cloud integration follows the general instructions above, with the following differences:
- You must select the API authorization scheme
- The API base URL field specifies that the Base URL of the Splunk Cloud API is required and recommends port 8089
The Events search field is required and pre-populates with the following, editable search string from which to pull security-related events:
(index=windows_events sourcetype=windows_security) OR (index=linux_logs sourcetype IN (linux_audit,linux_secure))- An optional Alerts search field, allowing you to enter a search string from which to pull security-related alerts

#
Splunk Enterprise integration
Configuring the Splunk Enterprise integration follows the general instructions above, with the following differences:
- You must select the API authorization scheme
- The API base URL field specifies that the Base URL of the Splunk Enterprise API is required and recommends port 8089
The Events search field is required and pre-populates with the following, editable search string from which to pull security-related events:
(index=windows_events sourcetype=windows_security) OR (index=linux_logs sourcetype IN (linux_audit,linux_secure))- An optional Alerts search field, allowing you to enter a search string from which to pull security-related alerts

#
Editing an integration
To edit the active/inactive status, description, API base URL, and/or API client credentials, follow the steps below.
Select the Edit button for any of your current integrations to open the Edit Integration right sidebar navigation.
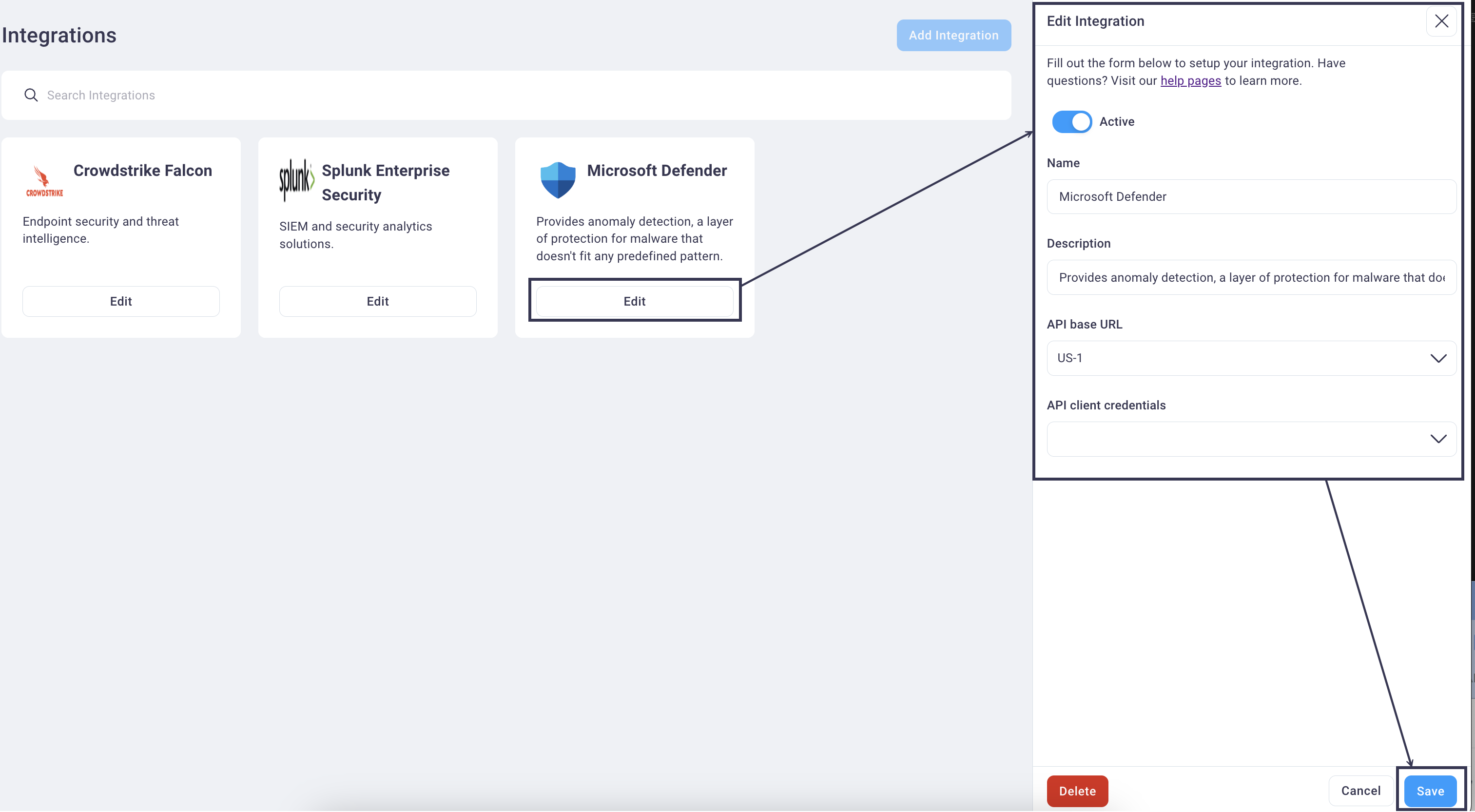
Edit any field values and select the Save button to save them and return focus to the main Integration page.

