#
DNS Records
DNS records are discovered by querying public DNS servers for each discovered Domain asset.
#
Accessing the DNS Records page
To access the DNS Records page, select or hover over EASM in the side navigation and then select DNS Records.
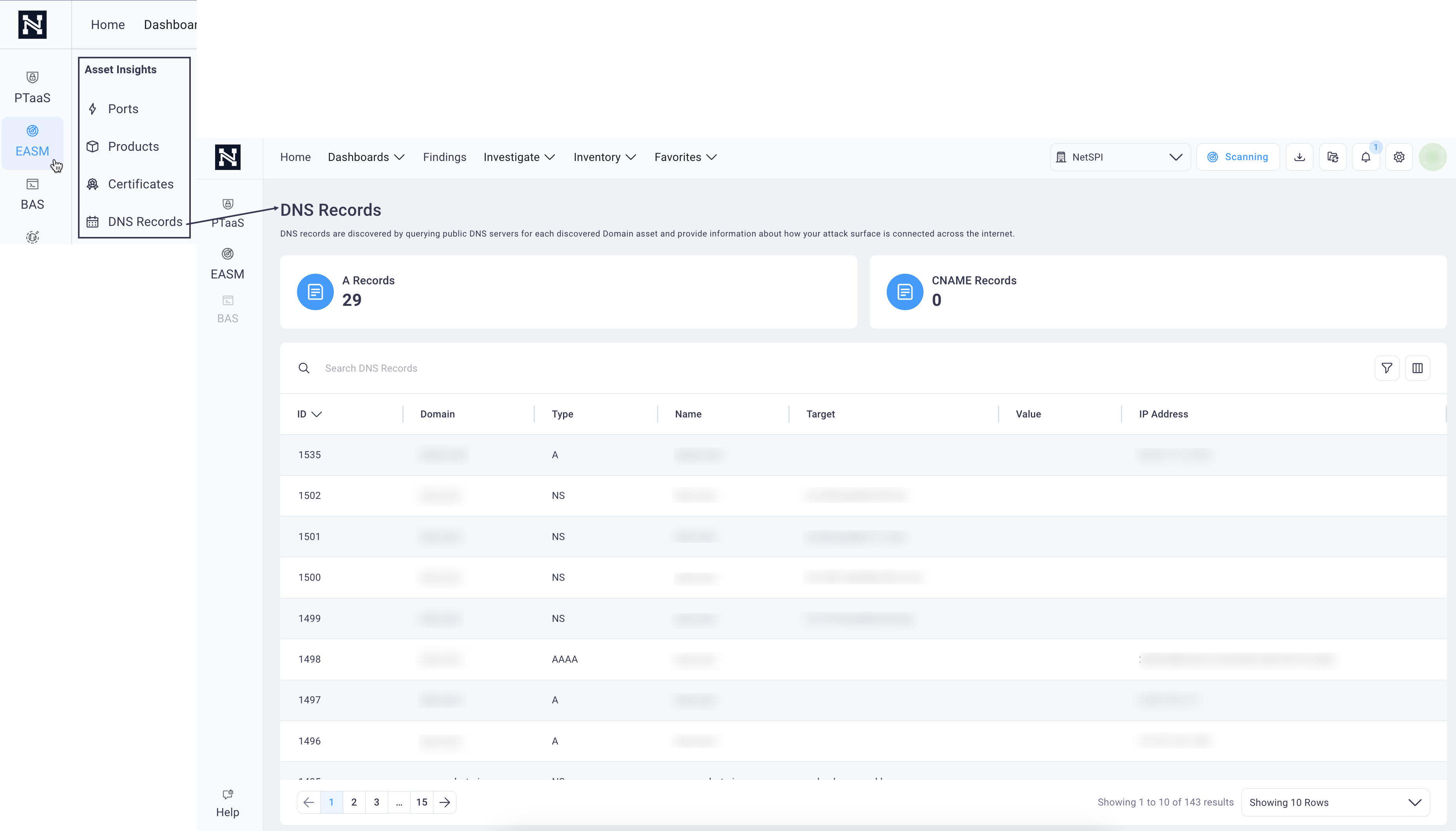
See the Search, Sort, and Filter tables section for customizing the table display and the Save applied filter as a preset to save your user-defined filters for reuse.
You can also select any of the DNS metrics cards to apply a filter to the table below that matches that metric criteria.

#
Record types
#
A Records
A records point a domain name to an IPv4 address. This can sometimes be a valuable source of identifying unknown IP addresses used across an attack surface, or for identifying high priority production assets.
#
AAAA Records
Like A records, AAAA records point a domain name to an IPv6 address.
#
CNAME Records
CNAME records allow you to redirect one domain name to another, commonly to prevent the necessity of rotating non-static IPs in A records. CNAMEs commonly expose internal or sensitive domains not commonly used by the public, or 3rd party platforms your organization may be using.
#
MX Records
MX records tell mail servers how to handle email requests sent to users using your domain. Misconfigurations in mail servers and MX records are common, allowing users to possibly abuse your mail systems or spoof emails as coming from your company.
#
TXT Records
TXT records are commonly used to prove domain ownership for 3rd parties you want to register your domain with. TXT records provide a significant amount of information about third party tools your company may be using that can be used to exploit exposures in your attack surface.
#
NS Records
NS records tell DNS servers who is responsible for responding to DNS queries about your domain name. Misconfiguration in nameservers can result in complete takeover of your domain name.
#
PTR Records
PTR records, sometimes referred to as reverse DNS or RDNS records allow internet users to take an IP address and resolve it to a domain name.
#
Mail Authentication Records
DMARC records, combined with SPF and DKIM, provide authentication mechanisms that help prevent email spoofing.
#
Others
NetSPI does not currently maintain records for SOA or SRV records, but they may be used during manual penetration testing of your network.

