#
Products
Third-party products comprise one of the most common attack vectors for threat actors. Well known and with documented exploits, most third-party tools, if not well patched, offer an easy mechanism to enter your internal network.
We identify over 1500 common technologies and manually escalate any discovered with publicly known vulnerabilities. Product discovery is performed by analyzing all exposed Ports, sending requests to them, and analyzing the responses for common patterns and fingerprints these technologies are known to respond with.
#
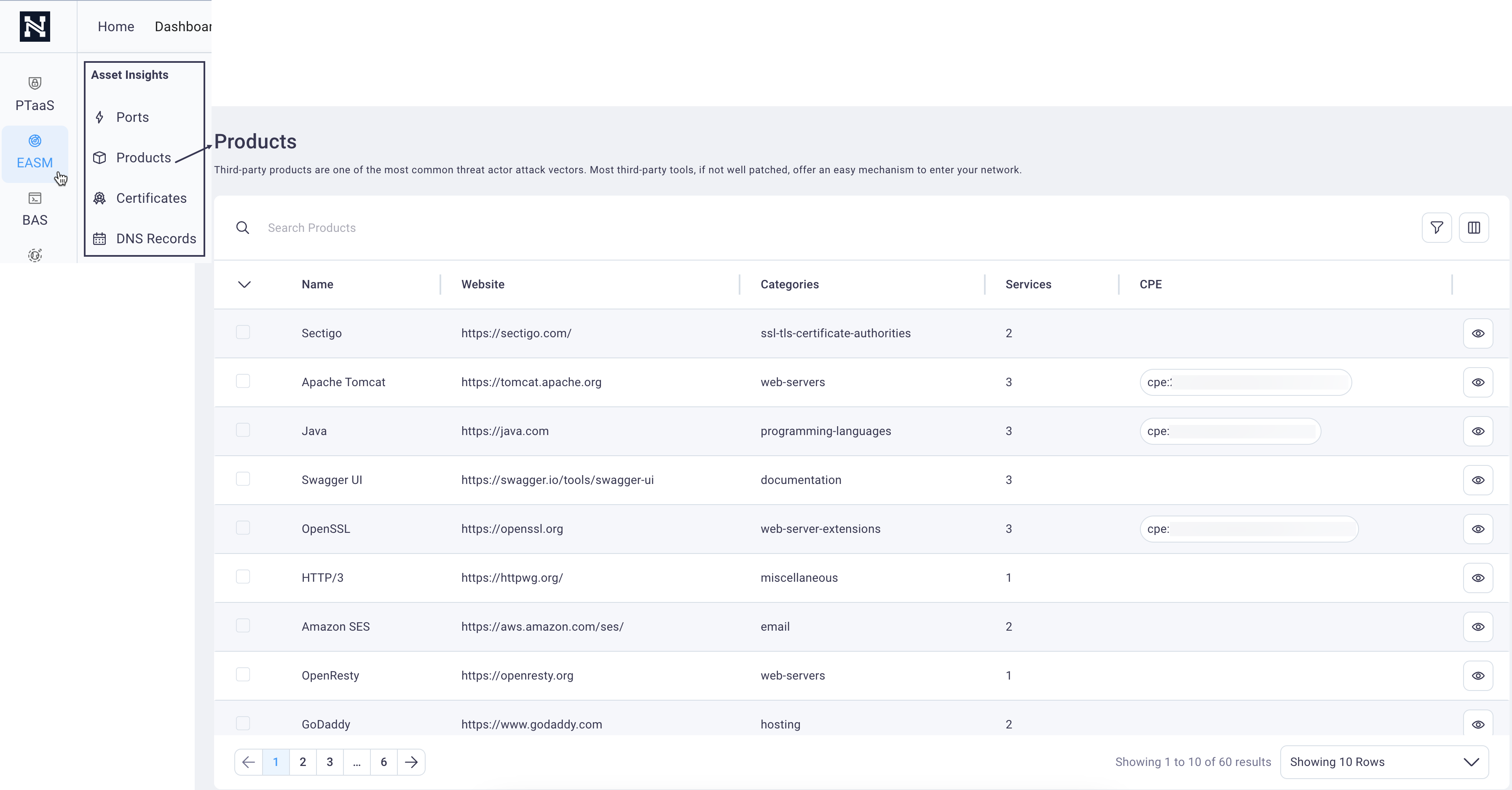
Accessing the Products page
Select (or hover over) EASM in the side navigation and then select Products to display the Products page.
#
Filtering the Products page and viewing details
Select the Filter icon
 to narrow the Products table results.
to narrow the Products table results.See the Search, Sort, and Filter tables section for customizing the table display and the Save applied filter as a preset to save your user-defined filters for reuse.
Select anywhere in a Product table row to display the Product details page in the right side slide-out panel in a condensed display.
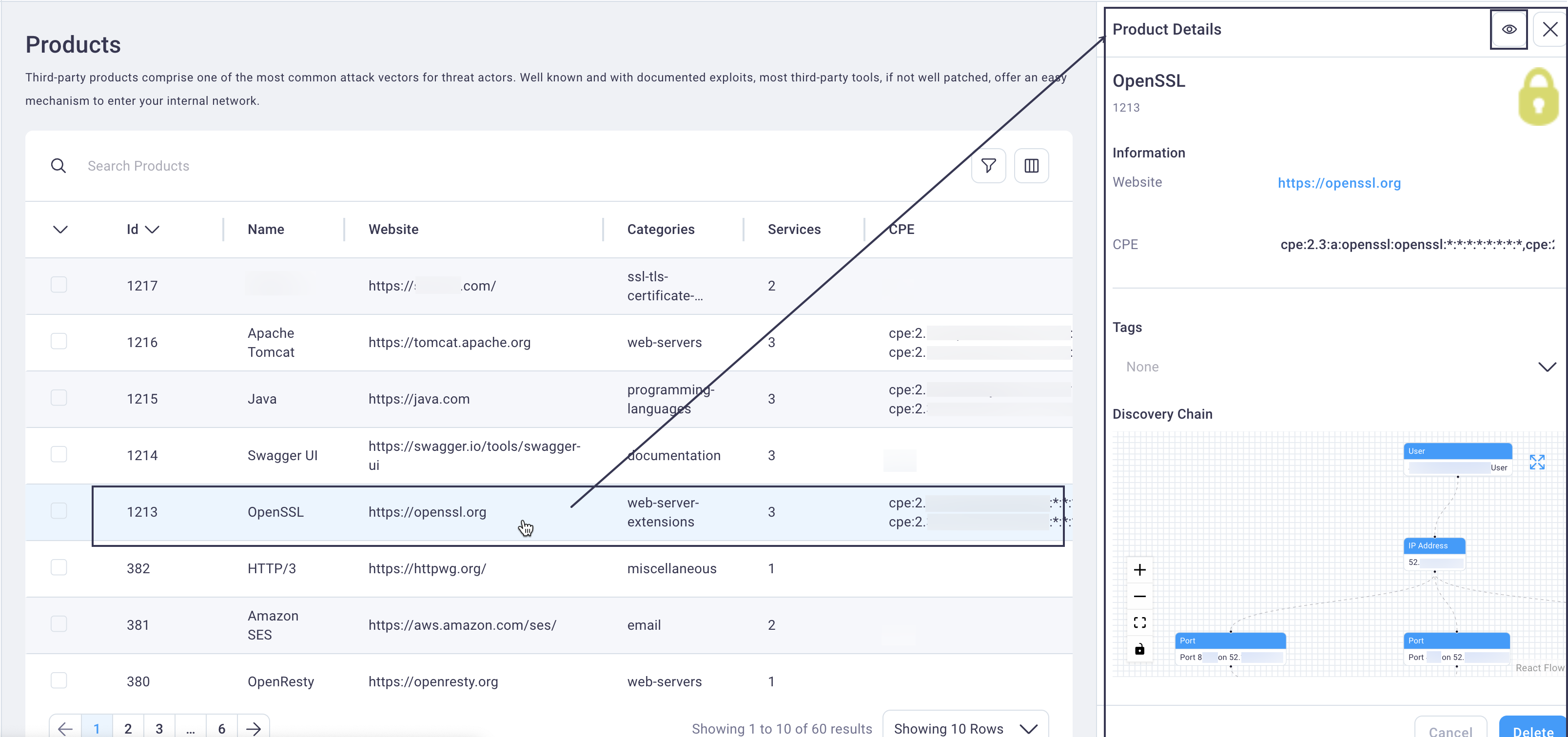
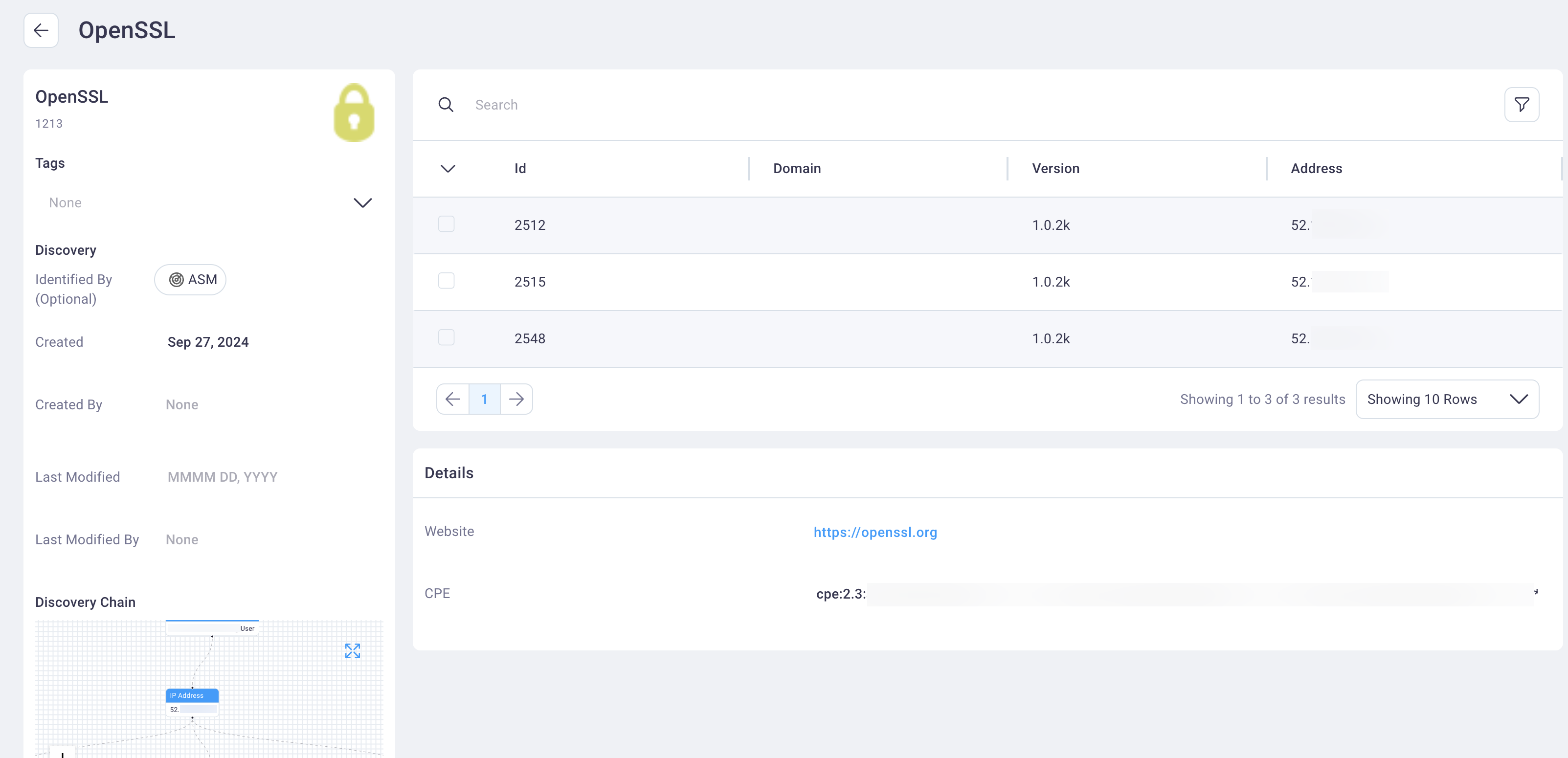
The Product Details page includes the product name, the discovery chain, a table of instances and locations of that product, and website and CPE information.
Note
Select the full-page icon
 to the far right on any row to
display a full-page view of the Product details. You can also select the full-page icon from the details
side page view.
to the far right on any row to
display a full-page view of the Product details. You can also select the full-page icon from the details
side page view.