#
BAS Integrations
The BAS Integrations page allows you to connect BAS with your other products. This empowers BAS to communicate with the third-party provider to determine if it was able to detect the actions taken when a procedure ran.
BAS supports integration with the following products.
BitDefender GravityZone XDR Carbon Black Cloud CrowdStrike Falcon DefenseStorm GRID Microsoft Defender Microsoft Sentinel Palo Alto Cortex XDR SentinelOne Singularity Splunk Cloud (with Splunk Enterprise Security)Splunk Enterprise (with Splunk Enterprise Security)
BAS integrations fall into two categories of capabilities.
Event Viewer: BAS finds events with a high-probability of relevance, and you provide the final acknowledgement and label for that event while associating it to a play.
Automatic Detection Categorization: BAS automatically labels/correlates events to the play.- Integrations with Automatic Detection Categorization also possess
Event Viewercapability
- Integrations with Automatic Detection Categorization also possess
#
Adding an integration
To add an integration, follow the general steps below. See the sections that follow for your exact integration for any specific details.
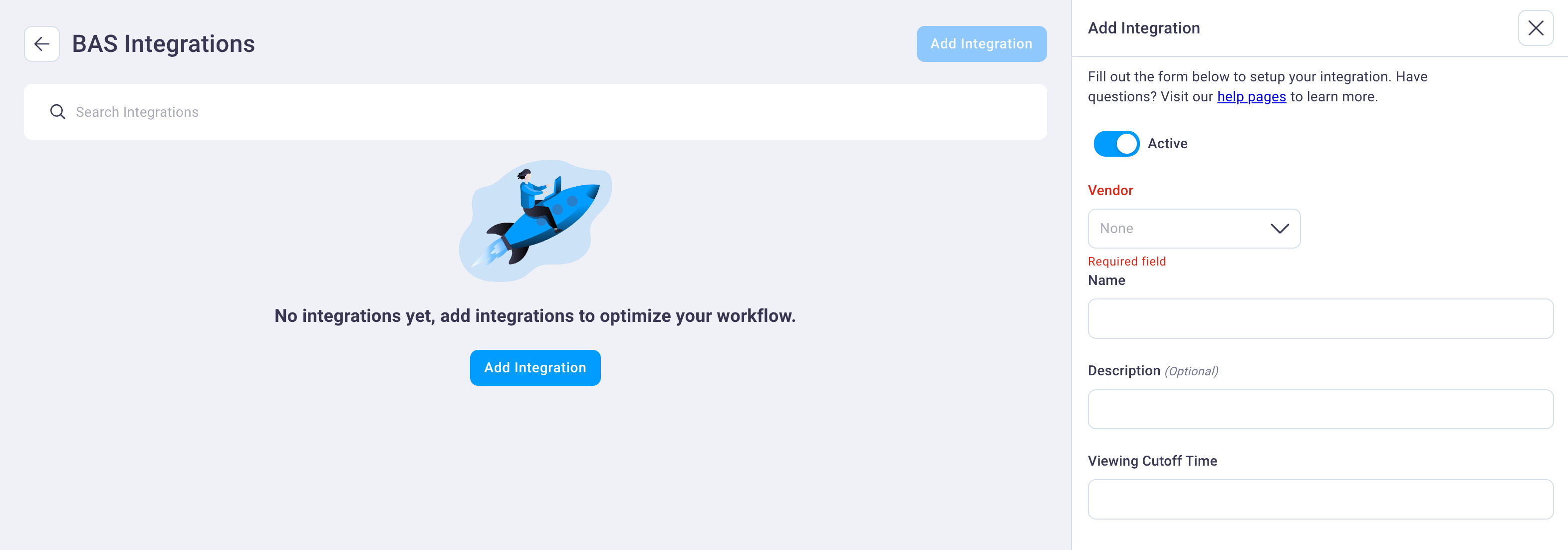
Select the Add Integration button at the top right of the page to display the Add Integration right sidebar navigation.
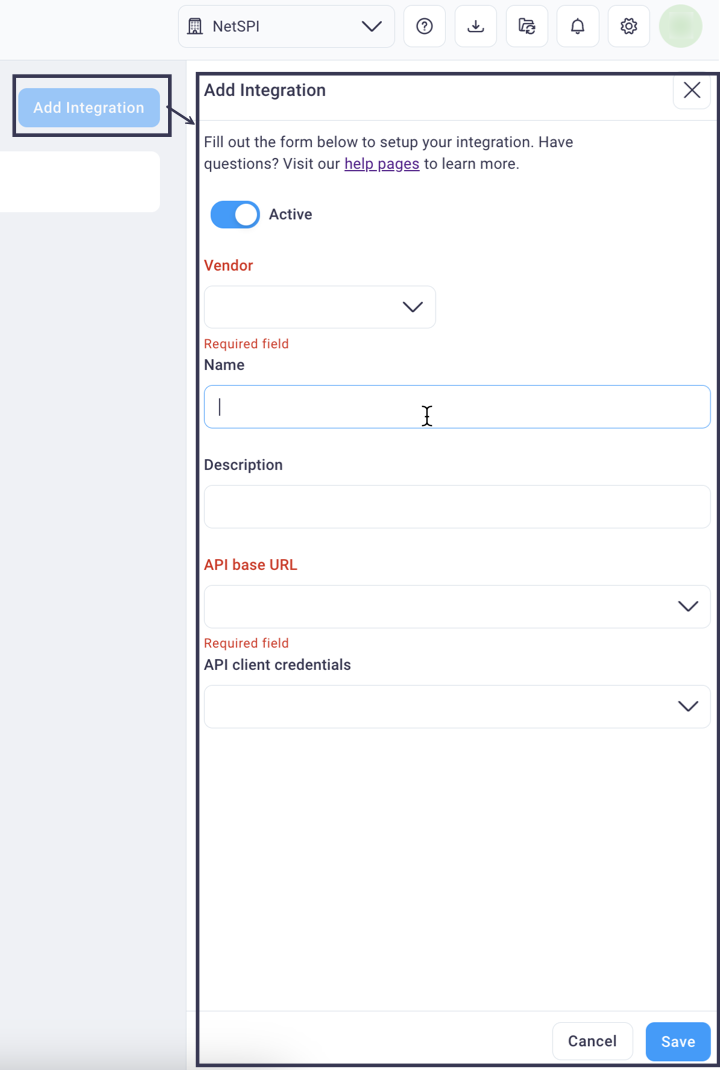
Select the Active slider to set the integration to active (blue) or inactive (gray).
Select the desired integration from the Vendor drop-down list.
Enter a name of your choice in the Name and Description fields.
Enter a value in the Viewing Cutoff Time field. This value, in seconds, represents the look-ahead time since a play was run that events are recorded, capturing or resulting in an event, alert, or detection time.
In the Credentials field group, select from the following options:
Select the Use Saved Credentials radio button if you have already created and saved credentials in the BAS Credential Management page. This option is selected by default and allows you to choose the credential from the API Client Credentials drop-down list
Select the Create New Credentials radio button to add your product's API credentials on the fly.
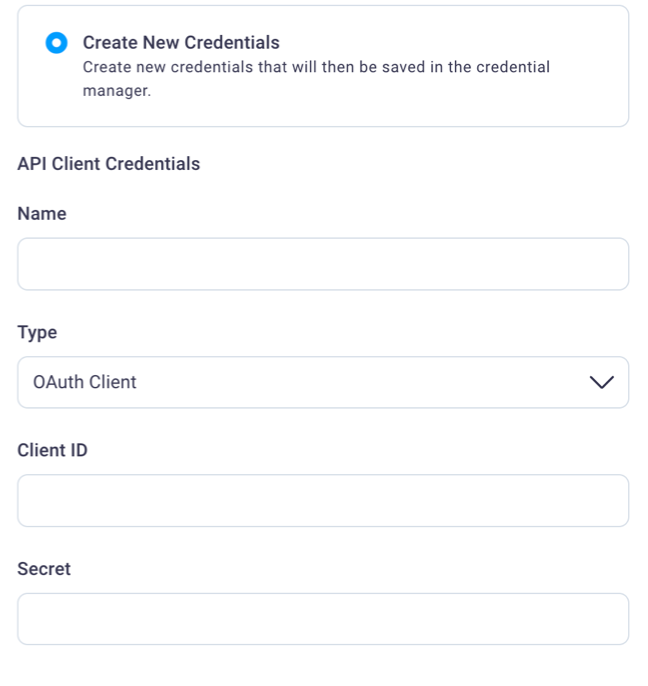
Select the Test Connection button to confirm your integration connection.
#
BitDefender GravityZone XDR
Capability: Automatic Play Verification
Configuring the BitDefender GravityZone XDR integration follows the general instructions above, with the following differences:
#
BitDefender GravityZone XDR settings
- API Access URL (required): Access URL of your BitDefender GravityZone XDR API.
- Company ID (required): Your BitDefender GravityZone XDR company ID.
#
BitDefender GravityZone XDR supported credential types
API Key [Token]
#
BitDefender GravityZone XDR required permissions and scopes
#
Carbon Black Cloud
Capability: Automatic Play Verification
Configuring the Carbon Black Cloud integration follows the general instructions above, with the following differences:
#
Carbon Black Cloud settings
- API Base URL (required): Base URL of your Carbon Black API.
- Organization Key (required): Your Carbon Black organization key.
- This key is found within your Carbon Black Cloud instance on the
API Accesspage underSettings.
- This key is found within your Carbon Black Cloud instance on the
#
Carbon Black Cloud supported credential types
API Key [ID and Secret]: Regular use; CommonOAUTH: When integrating through VMWare
#
Carbon Black required permissions and scopes
The API key created must have an access level with the following permissions:
Alerts Category: readThreatMetadataNotesThreatHuntGeneral information
Search: create, read, executeEvents
#
CrowdStrike Falcon
Capability: Automatic Play Verification
Configuring the CrowdStrike integration follows the general instructions above, with the following differences:
#
CrowdStrike Falcon settings
- API Base URL (required): Base URL of your CrowdStrike API.
#
CrowdStrike Falcon supported credential types
OAUTH
#
CrowdStrike Falcon required permissions and scopes
Alerts Scope: readDetections Scope: read
#
CrowdStrike Falcon integration walkthrough
This integration requires the Oauth Client credential type. Please refer to the CrowdStrike documentation for generating these credentials in Falcon.
Note
When creating an API Client, you will need to enable Read access for the Alerts Scope and Detections Scope.
Select Let's Get Started in the walkthrough below to see how to create a CrowdStrike integration with BAS.
#
DefenseStorm GRID
Capability: Automatic Play Verification
Configuring the DefenseStorm GRID integration follows the general instructions above, with the following differences:
#
DefenseStorm GRID settings
- API Base URL: Base URL of your DefenseStorm GRID API.
#
DefenseStorm GRID supported credential types
API Key [ID and Secret]
#
DefenseStorm GRID required permissions and scopes
The input token created must be for the API.
#
Microsoft Defender
Capability: Event Viewer
Configuring the Microsoft Defender integration follows the general instructions above, with the following differences:
#
Microsoft Defender settings
- Tenant ID (required): Directory (tenant) ID
- Found on the
Application Registrationpage underEssentialsin Microsoft Security
- Found on the
#
Microsoft Defender supported credential types
OAUTH
#
Microsoft Defender required permissions and scopes
The client secrets created must be for an Application that has been assigned the following permissions in
Microsoft Entra ID:
Microsoft GraphSecurityAlert.Read.All: applicationSecurityEvents.Read.All: applicationSecurityIncident.Read.All: applicationThreatHunting.Read.All: applicationUser.Read: delegated
#
Microsoft Sentinel
Capability: Event Viewer
Configuring the Microsoft Sentinel integration follows the general instructions above, with the following differences:
#
Microsoft Sentinel settings
- Tenant ID (required): Directory (tenant) ID
- Found on the
Application Registrationpage underEssentialsin Microsoft Security
- Found on the
#
Microsoft Sentinel supported credential types
OAUTH
#
Microsoft Sentinel required permissions and scopes
The client secrets created must be for an Application that has been assigned the following permissions in
Microsoft Entra ID:
Microsoft GraphSecurityAlert.Read.All: applicationSecurityEvents.Read.All: applicationSecurityIncident.Read.All: applicationThreatHunting.Read.All: applicationUser.Read: delegated
#
Palo Alto Cortex XDR
Capability: Automatic Play Verification
Configuring the Palo Alto Cortex XDR integration follows the general instructions above, with the following differences:
#
Palo Alto Cortex XDR settings
#
Palo Alto Cortex XDR supported credential types
API Key [ID and Secret]: Can be set toAdvancedorStandard
#
Palo Alto Cortex XDR required permissions and scopes
The API key created must have view access for the following permissions:
Components->INVENTORY->Agents->Agent AdministrationComponents->CASES & ISSUES
#
SentinelOne Singularity
Capability: Event Viewer
Configuring the SentinelOne Singularity integration follows the general instructions above, with the following differences:
#
SentinelOne Singularity settings
- API Base URL (required): Base URL of your SentinelOne Singularity API.
#
SentinelOne Singularity supported credential types
API Key [Token]
#
SentinelOne Singularity required permissions and scopes
The API key created must be for a User or Service user assigned a Role with the following permissions:
Endpoint Threats: viewThreat Intelligence: view
#
Splunk Cloud
Capability: Automatic Play Verification
Configuring the Splunk Cloud integration follows the general instructions above, with the following differences:
#
Splunk Cloud settings
- API Authorization Scheme (required):
- Splunk
- Oauth (Bearer)
- API Base URL (required): Base URL of your Splunk Cloud API
- Splunk typically recommends the default port
8089
- Splunk typically recommends the default port
- Events search (required): Pre-populates with the following, editable search string from which to pull
security-related events:
(index=windows_events sourcetype=windows_security) OR (index=linux_logs sourcetype IN (linux_audit,linux_secure))- This search string is a typical default configuration for Splunk Enterprise Security
- Alerts search: Optional search string from which to pull security-related alerts
#
Splunk Cloud supported credential types
API Key [Token]
#
Splunk Enterprise
Capability: Automatic Play Verification
Configuring the Splunk Enterprise integration follows the general instructions above, with the following differences:
#
Splunk Enterprise settings
- API Authorization Scheme (required):
- Splunk
- Oauth (Bearer)
- API Base URL (required): Base URL of your Splunk Enterprise API
- Splunk typically recommends the default port
8089
- Splunk typically recommends the default port
- Events search (required): Pre-populates with the following, editable search string from which to pull
security-related events:
(index=windows_events sourcetype=windows_security) OR (index=linux_logs sourcetype IN (linux_audit,linux_secure))- This search string is a typical default configuration for Splunk Enterprise Security
- Alerts search Optional search string from which to pull security-related alerts
#
Splunk Enterprise supported credential types
API Key [Token]
#
Editing an integration
To edit the active/inactive status, description, API base URL, and/or API client credentials, follow the steps below.
Select the Edit button for any of your current integrations to open the Edit Integration right sidebar navigation.
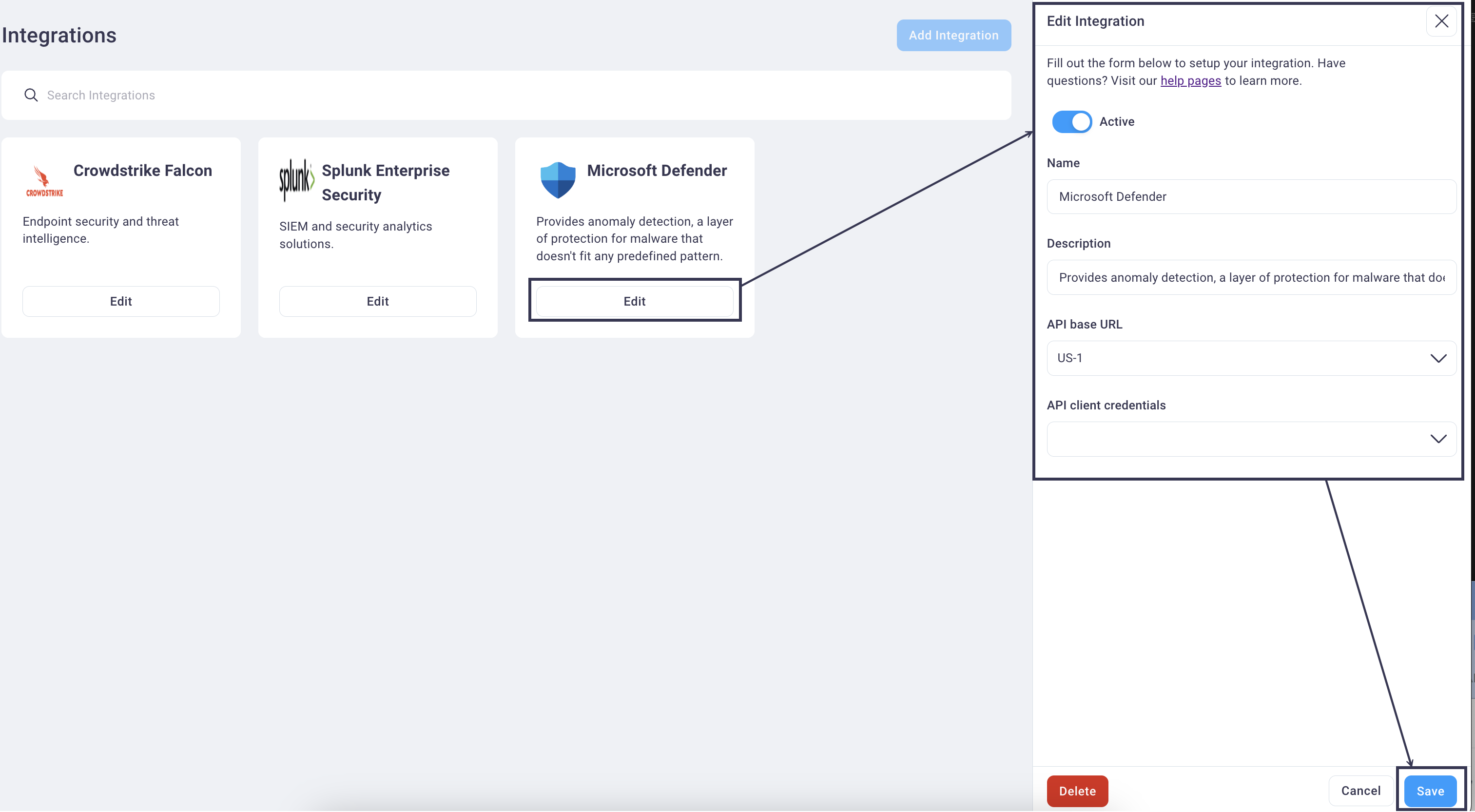
Edit any field values and select the Save button to save them and return focus to the main Integration page.

