#
AWS Organizations
The NetSPI Platform's CAASM module has a broad integration with Amazon Web Services (AWS) Organizations.
AWS Organizations allow you to centrally manage and govern many AWS accounts. If you only have several AWS accounts or do not use AWS Organizations, you should refer to the instructions on adding a single AWS account by default.
#
Supported asset types
The AWS Organizations integration provides the NetSPI Platform visibility into the following asset types:
- Networks
- Systems
- IPV4 addresses
- Cloud resources: IAM User, IAM Role, Cloud Account, S3, Lambda, RDS, ALB, NLB, WAF
#
Data run frequency
The AWS Organizations integration pulls data at minute 30 past every sixth hour (e.g, 12:30, 6:30, 12:30, etc.).
#
Endpoints used
The following endpoints are used in this AWS integration.
#
EC2 (Elastic Compute Cloud)
describe_regions
describe_subnets
describe_images
describe_instances
describe_iam_instance_profile_associations
#
ECS (Elastic Container Service)
list_clusters
describe_clusters
list_services
describe_services
list_task_definitions
describe_task_definition
#
ELB (Elastic Load Balancer)
describe_load_balancers
#
IAM (Identity and Access Management)
list_users
list_roles
list_groups
list_policies
list_mfa_devices
list_user_policies
list_role_policies
list_groups_for_user
list_attached_user_policies
list_attached_role_policies
get_role_policy
get_user_policy
get_group_policy
get_policy_version
get_instance_profile
#
Lambda
list_functions
#
RDS (Relational Database Service)
describe_db_instances
#
S3 (Simple Storage Service)
list_buckets
head_bucket
#
Security Hub
list_finding_aggregators
get_finding_aggregator
get_findings
#
WAF (Web Application Firewall)
list_web_acls
#
Workspaces
describe_workspace_bundles
#
Supported AWS services
This AWS integration supports the following AWS services.
Requirements
At least one of these products must be properly licensed in order for the integration to work.
- EC2
- S3
- VPC
- IAM
- Lambda
- RDS
- WAF
- ELB
- ECS
- Workspaces
- Security Hub
Similar to the other NetSPI Platform integrations, the AWS integration is read-only and does not perform actions to configure systems or otherwise change anything about your AWS environment.
#
Required permissions
This integration requires:
- An AWS trust relationship between the NetSPI Platform and your AWS environment
- A new role in your AWS environment
#
Configuration steps
Use the section below for configuring AWS Organizations to integrate with the NetSPI Platform CAASM module.
#
Role Creation for AWS Organizations
This guide provides instructions on how to use a CloudFormation template to upload policies to all sub-accounts in your AWS Organization. CAASM customers with many sub-accounts can use this method to create roles and trust policies in their sub-accounts.
Before following these instructions to configure AWS sub-accounts, you must follow steps 1-8 on the single AWS integration page using a role name of "NetSPI-CAASM-ExecutionRole" to add your AWS Organization root account manually. Save the externalId value for reuse during StackSet creation here.
Do not add the Organization root account in the CAASM UI until you have completed all of the steps below to configure permissions in sub-accounts.
- Save the following CloudFormation template to a file, e.g.,
netspi-caasm-aws-organization.yaml:
AWSTemplateFormatVersion: "2010-09-09"
Description: "
StackSet template to create roles and permissions inside Organization sub-accounts
necessary for the NetSPI CAASM AWS Cloud Integration at the Organization level.
"
Parameters:
ExternalId:
Type: String
Description: "
ExternalId to be used in the AssumeRolePolicyDocument. Reuse the externalId
created when setting up permissions in the root Organization account.
"
Resources:
CAASMExecutionRole:
Type: AWS::iam::Role
Properties:
RoleName: "NetSPI-CAASM-ExecutionRole"
AssumeRolePolicyDocument:
Version: "2012-10-17"
Statement:
- Effect: Allow
Principal:
AWS: "arn:aws:iam::339712971568:root"
Action: "sts:AssumeRole"
Condition:
StringEquals:
"sts:ExternalId": !Ref ExternalId
ManagedPolicyArns:
- arn:aws:iam::aws:policy/SecurityAudit- In the AWS console for your Organization account, navigate to CloudFormation > StackSets.
- Select "Create StackSet".
- Select "Service-managed permissions", "Template is ready", and "Upload a template file", selecting the file saved in step 1.
- Reuse the
externalIdvalue created in the Single Account AWS Integration steps used for the AWS Organization. - Proceed with StackSet creation and select "Submit".
- Once the StackSet has successfully been deployed, go into an AWS sub-account console and confirm that the role name created is identical to "NetSPI-CAASM-ExecutionRole".
#
Add your AWS Organization account to the NetSPI Platform's CAASM Module
Use the steps below to configure the AWS Integration in the NetSPI Platform.
Log into the NetSPI Platform as a Client Admin user.
Navigate to Settings -> CAASM Integrations to display the Integrations page.
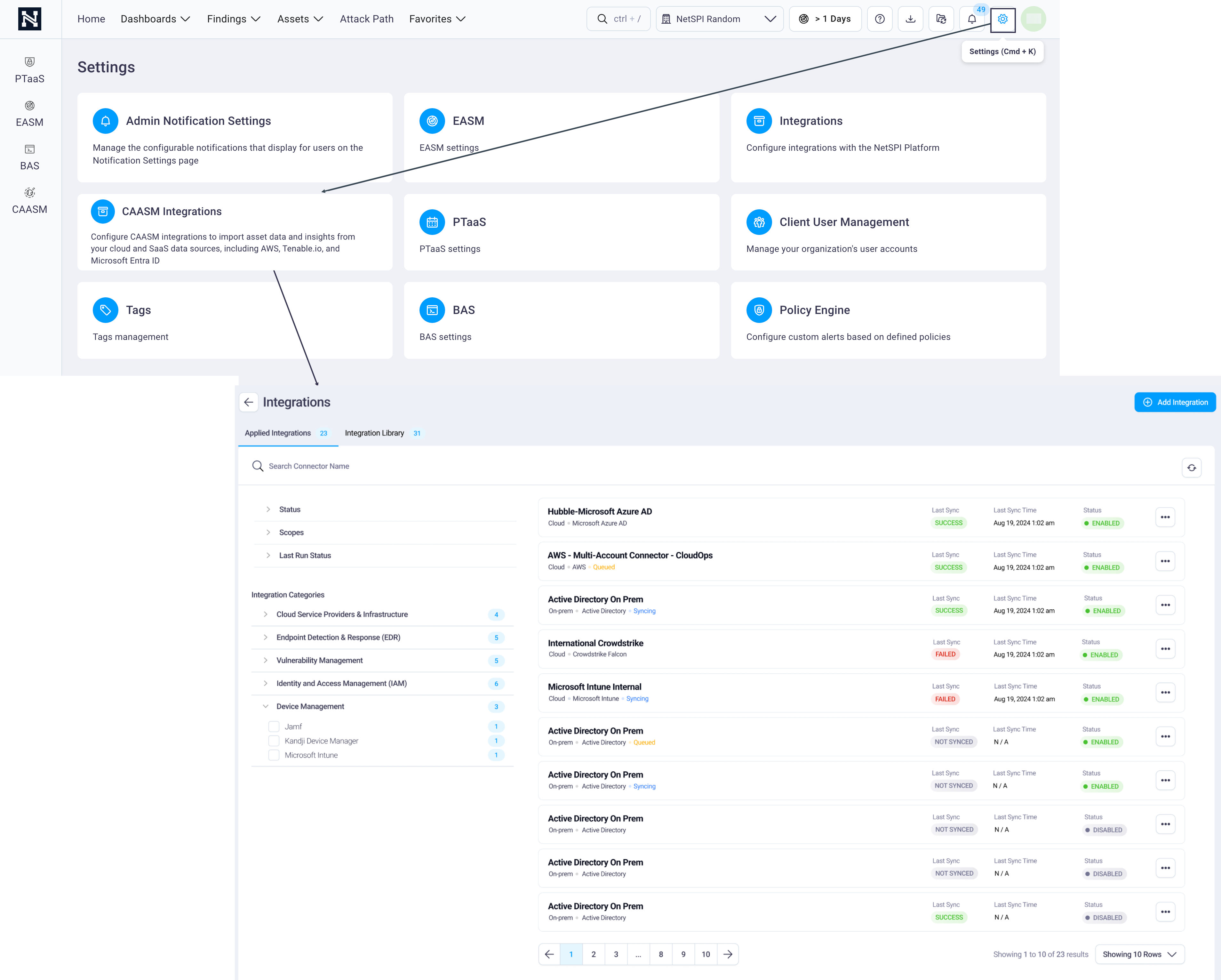
Select the Integration Library tab -> Integration Categories / Cloud -> AWS.

This brings the AWS integration card into focus.
Note
You can also locate the integration card by:
- Scrolling down the page on the Integration Library tab
- Filter the integration options displayed by selecting any of the other left navigation choices besides Integration Categories, e.g., by Modules or Integration Scopes (cloud or on premise)
- Enter the integration name in the Search integration bar
Select the Add button on the AWS card to display the AWS integration configuration page.
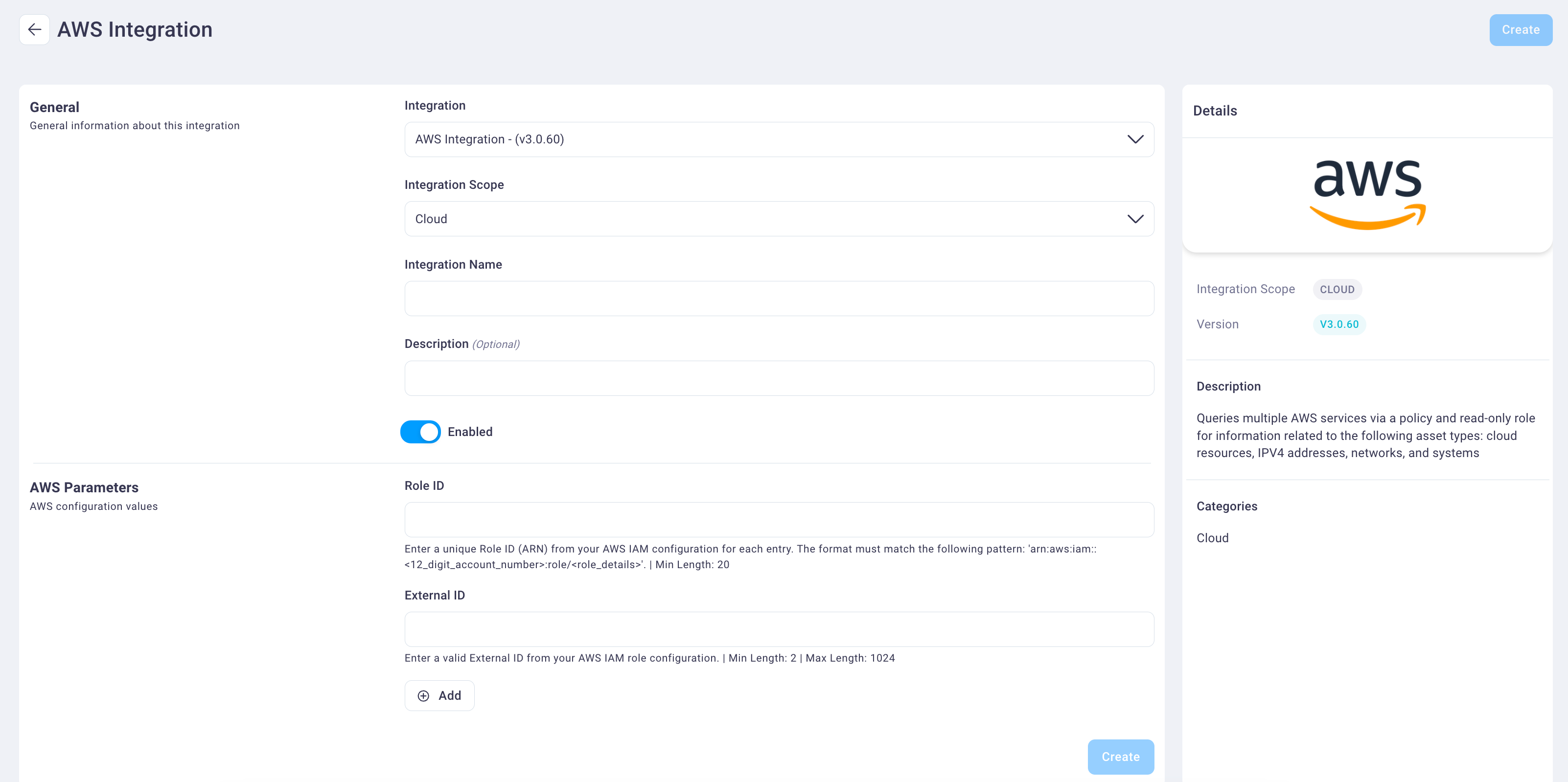
Select and enter values for the following fields.
Select the integration type from the Integration drop-down list. In this case, AWS, which is already selected by default.
Select the integration scope from the Scope drop-down list. The AWS integration can only run on a cloud scope, which was configured by NetSPI and Cloud displays as the default value.
Enter an integration name and description in the Integration Name and Description fields.
Select the Enabled slider button to display as either on (blue) or off (light gray).
Select the AWS Organization Root Account slider button when your integration is for an AWS Organization.
Paste the ARN copied from Step 8 of the Step two: AWS role configuration above into the Role ID field.
Enter or copy/paste the random External ID generated in Step 4 of the Step two: AWS role configuration above to the External ID field.
If additional ARN's need to be added, select the Add button to display additional Role ID and External ID fields.
Select Create to create the integration. The new integration now displays on the Applied Integrations tab with its statuses: current and last run, last run time, and status (enabled/disabled).
AWS Docs Ref: https://docs.aws.amazon.com/IAM/latest/UserGuide/tutorial_cross-account-with-roles.html

