#
CAASM
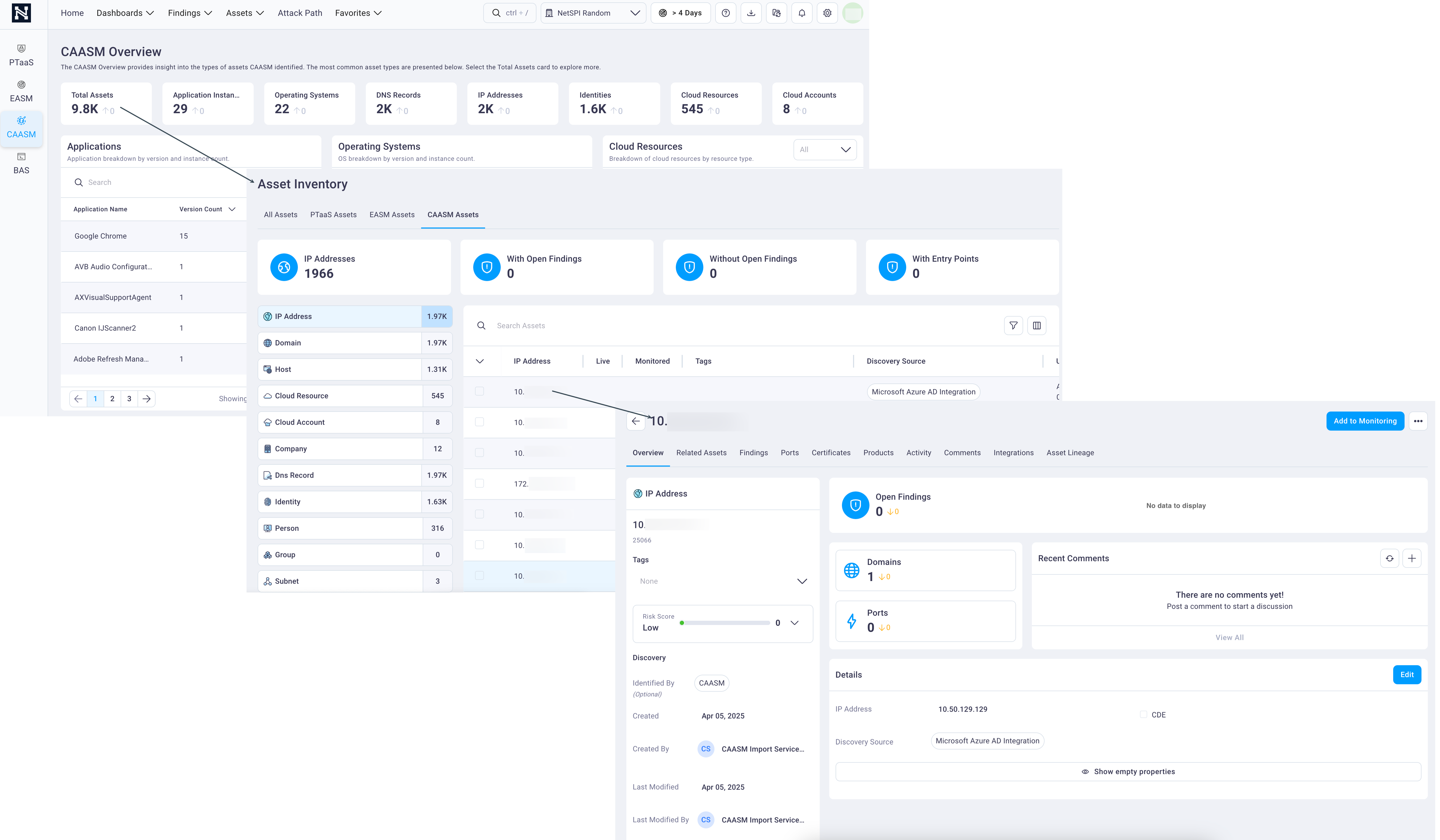
The NetSPI CAASM (Cyber Asset Attack Surface Management) module brings all of your diverse digital cloud and SaaS assets into a single view and then layers configuration, vulnerability, and risk context. This provides real-time asset identification, risk-based remediation, and control gap detection. Reducing your likely cyber attacks and an enhanced security posture is the result.
#
Why NetSPI CAASM?
NetSPI CAASM looks beyond your externally-identifiable attack surface. (See our EASM module for external asset discovery and monitoring.)
NetSPI CAASM digs deeper by connecting to, and aggregating, your existing security tool data to define risk throughout your entire network. The result is a more complete asset inventory with intelligence beyond any single tool capability.
#
Challenge: Lack of visibility
Most organizations lack full visibility into their cyber assets. From shadow IT and unmanaged endpoints to outdated software and unpatched systems, security teams are often unaware of what's in their environment — or where. Without real-time, accurate asset intelligence, risks go undetected, vulnerabilities remain unaddressed, and attackers find open doors. NetSPI CAASM delivers a holistic view of known and unknown internal cloud and SaaS assets and their related risk.
#
Challenge: Identify control coverage gaps
Security controls are only effective if they're deployed and working as expected — but most companies don't know where those controls are missing or misconfigured. From patching and EDR to MFA and logging, blind spots in control coverage create dangerous gaps. Without a continuous, trustworthy way to validate protection, you're operating with a false sense of security. NetSPI CAASM maps security control coverage across your assets and discovers the gaps.
#
Challenge: Prioritization and remediation
Modern security teams are overwhelmed with alerts but underwhelmed with insight. Knowing a vulnerability exists is only step one — knowing whether it matters right now is what enables smart, focused remediation. But most tools fail to deliver the context needed to separate noise from critical issues. The result? Wasted effort, missed threats, and persistent risk. NetSPI CAASM enables risk-based prioritization and remediation so you can protect your most valuable assets and align your organization with ease.
#
The solution: Turning fragmented signals into actionable security
While most cybersecurity platforms deliver isolated data points, our platform takes a different approach: we unify, contextualize, and surface what matters — all through seamless API integration with the tools you already use. By plugging into your existing environment, our solution connects the dots between asset inventory, security control validation, and prioritized remediation so your security team can focus on actions, not analysis.
Here's how.
#
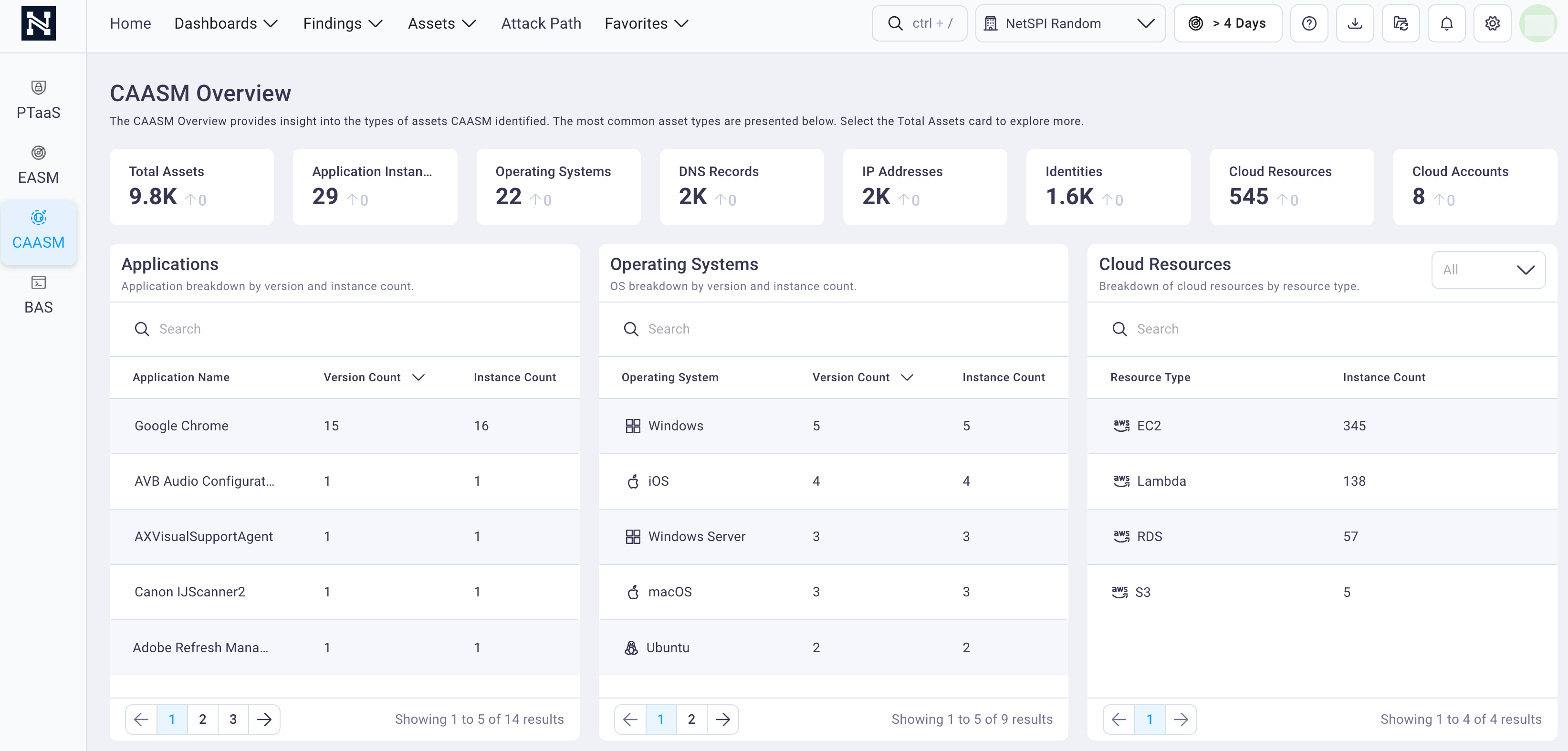
See everything — instantly
We integrate with your existing infrastructure — asset management tools, configuration databases, endpoint tools, and more — to give you real-time visibility into every device, application, and system in your environment. You'll know what's installed, where it lives, and whether it's up-to-date — all without deploying a new agent or rebuilding your stack.
Outcome
A living, continuously updated asset map that eliminates blind spots and sets the foundation for risk-based security.
#
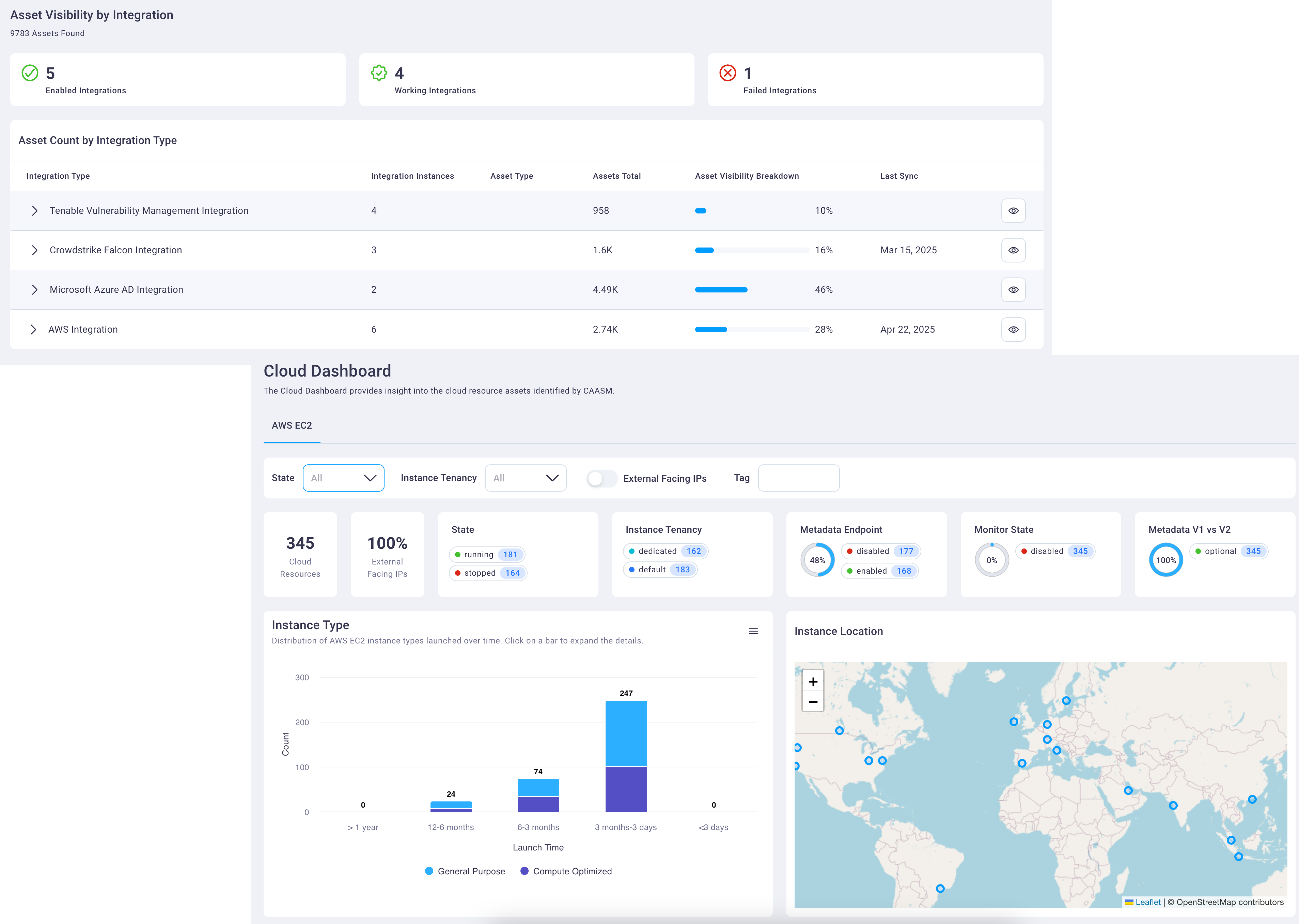
Spot the gaps before attackers do
We continuously audit your control coverage across your environment — without requiring manual checks or guesswork. Whether it's missing EDR agents, unpatched systems, or misconfigured logging, we surface exactly where controls are failing or missing, so you can close the gaps before they're exploited.
Outcome
Assurance that your protections are where they should be — and awareness when they're not.
#
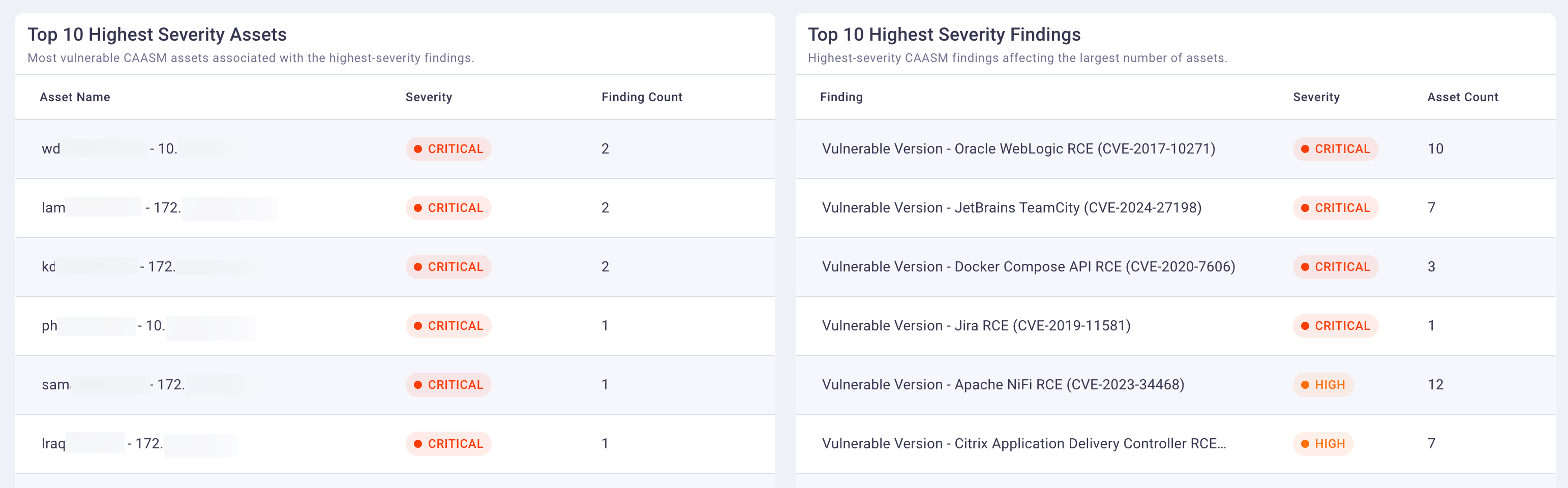
Prioritize what actually matters
Our platform brings context to vulnerability data by correlating asset information, control posture, and threat intelligence. We don't just tell you what's broken — we show you which issues pose the greatest risk right now based on business impact, exposure, and exploitability.
Outcome
Clear, defensible remediation priorities your team can act on — and prove value for.
Security teams don't need more noise — they need clarity, context, and confidence. With our API-first platform, you can finally take control of your cybersecurity posture, cut through the fog, and move from reactive firefighting to proactive security.

